Products
Discover Our Products that Guiding the Future
Products
Kafein Technology SolutionsData Touch
Data Touch combines the information gathered from database discovery and activity monitoring applications to track data in a secure way and analyze them with various built-in features. Data Touch enables users to gain a quick look at the data by visualizing them with graphs and maps.
Effectively tracking sensitive data is pivotal for safeguarding personal information and mitigating data misuse cases, particularly within extensive data repositories where sensitive data can be challenging to monitor. To address this challenge, a robust solution is essential for ensuring the meticulous tracking of sensitive data. Introducing Data Touch (DT), a cutting-edge tool seamlessly integrated with database discovery and activity monitoring applications, harnessing the combined insights from both platforms. Data Touch empowers users with a diverse array of analytical capabilities, enhancing their data comprehension and enabling more informed data-driven decisions, all while upholding the paramount principles of data security and privacy. DT is designed to address two core concerns:
- Monitoring sensitive data,
- Regulating data usage.
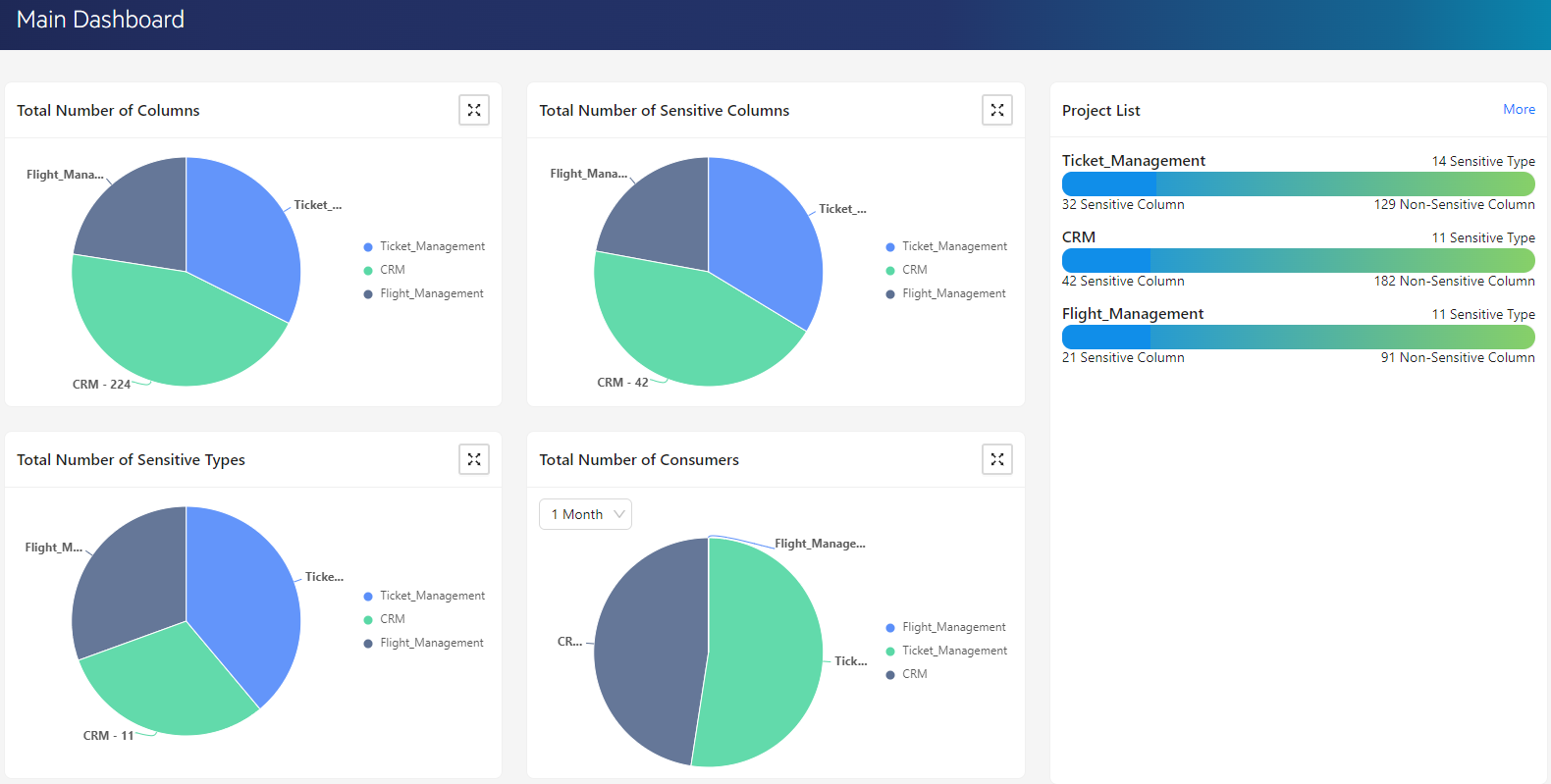
By leveraging classified data from database discovery application—categorized into sensitive and non-sensitive—DT produces visual representations using corresponding project names, displayed through intuitive charts. The product's primary dashboard page offers a concise overview of the data content from the ten most recent scanned projects, enabling easy access to critical information.
Data Touch Tool Capabilities:
- Analyze previously detected and classified data (sensitive and non-sensitive), and visualize them on graphs
- Showing the access of each application to any data in the given time interval and finding out from whom and how the data is used with all query details
- Tracking the lineage of data and visualizing the whole life cycle of it
- Reporting (all visually provided data)
- Data heatmaps
- Abnormal user behavior detection through AI and machine learning
Data Touch Features:
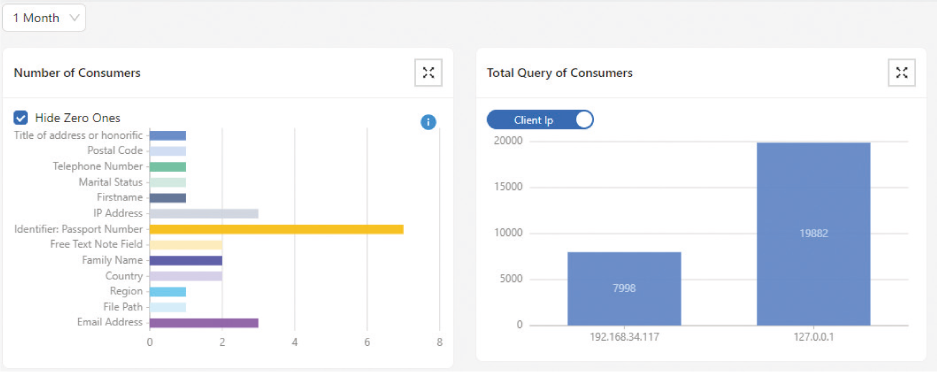
- Visualization: Shows all projects (from Discovery) in the same environment with detailed information on purpose-built charts. It ranks the projects according to their sizes and creates graphs of classified data (sensitive and non-sensitive), sensitive types and consumers on the dashboard.
- Data Usage: Shows projects (scanned by Discovery), consumers (who touched the data), in detail how and when they touched. By entering a date range, these details can be filtered. Tables can be filtered and exported via Excel.
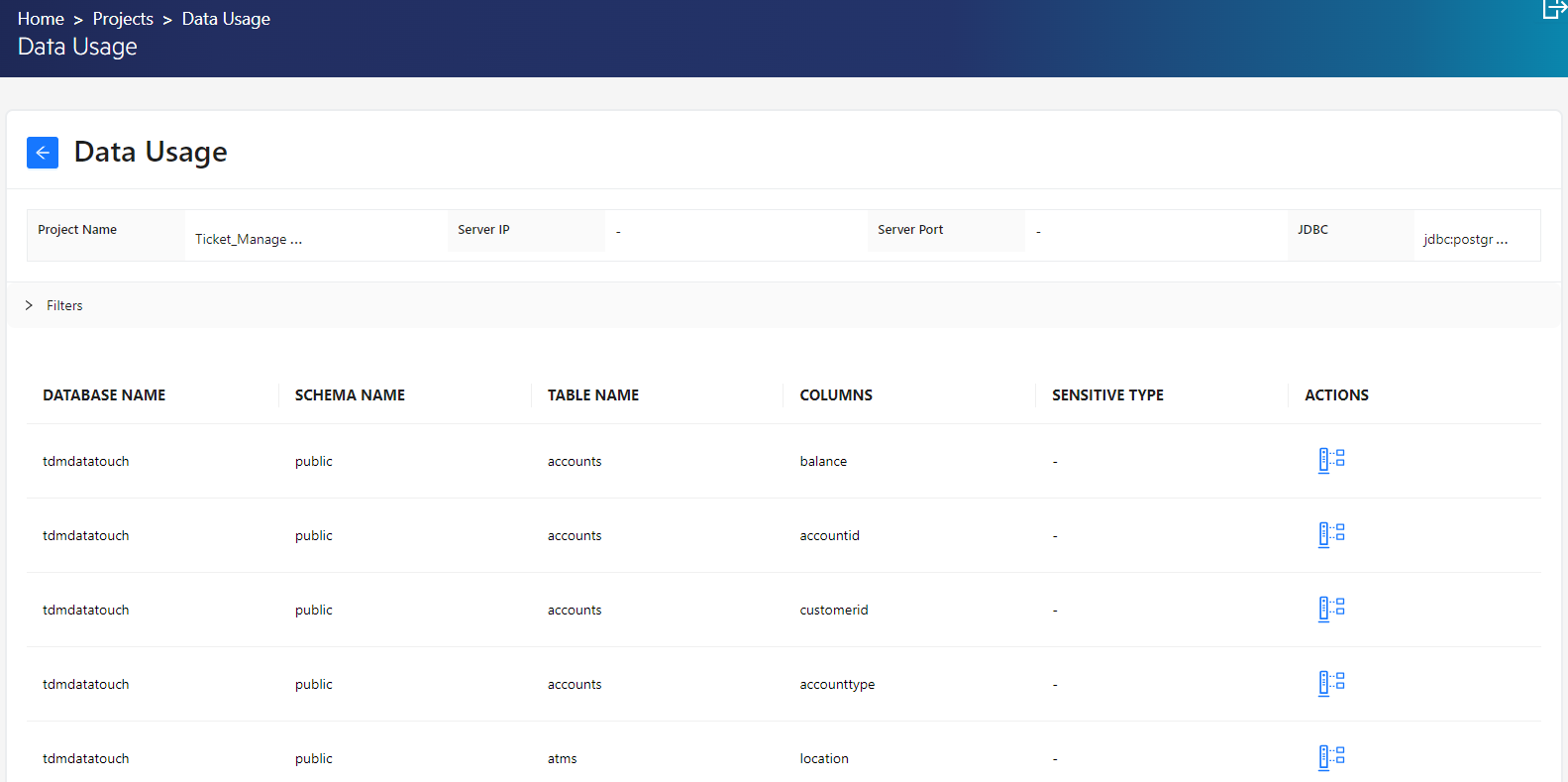
- Data Analysis: Shows the details of the queries for the project in three
ways:
- Query details,
- Queries made,
- Queries for sensitive types.
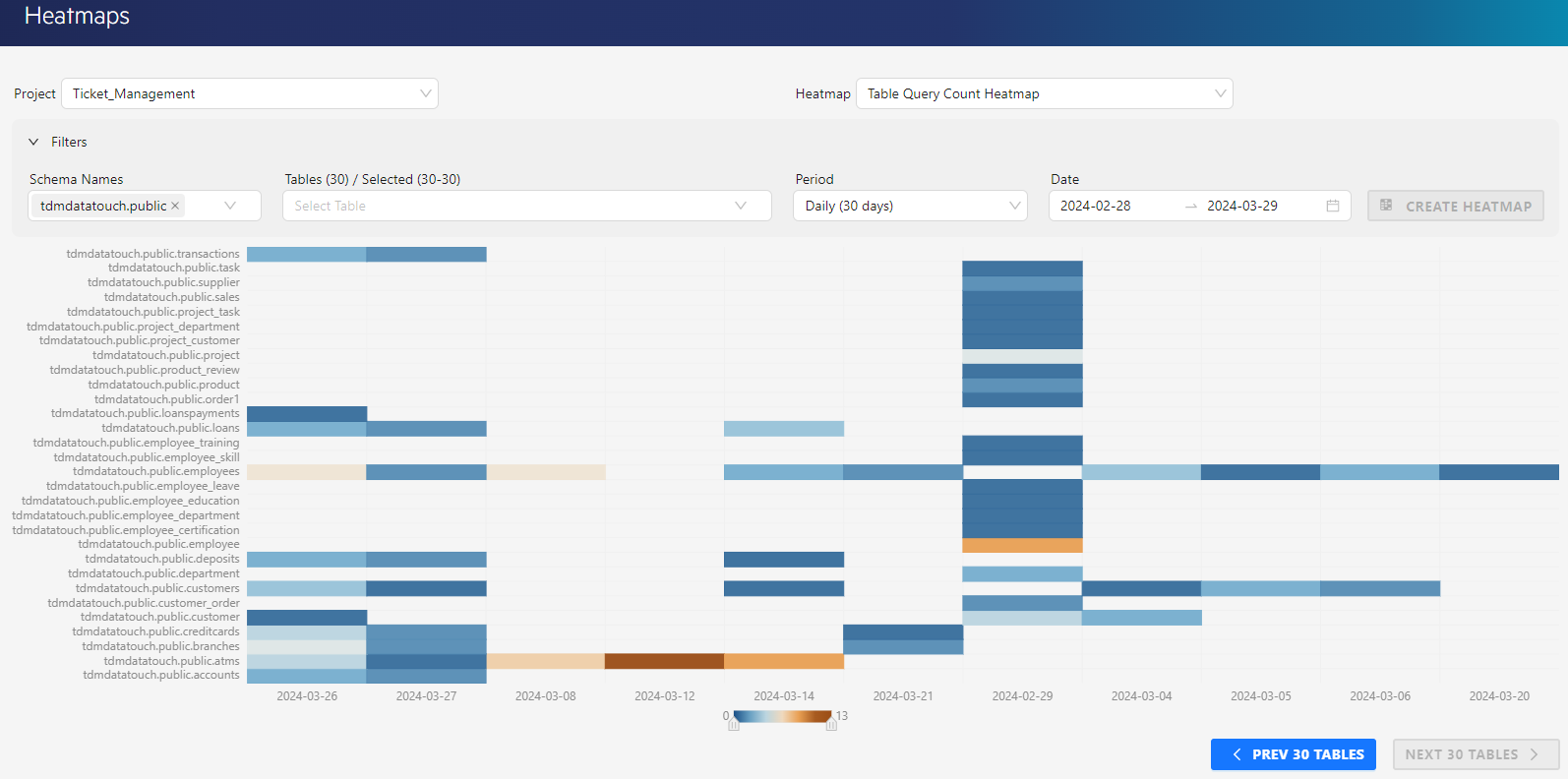
- Data Heatmaps: Creates different heatmaps with predefined options for more detailed analysis of all kinds of data within the application.
- Table Query Count Heatmap: Shows the total query number for each table for a specific date.
- Application Count Heatmap: Shows the total query number accessed from each application to each table.
- Table Action Type Count Heatmap: Shows the total query number by action type (select, update, delete, etc.) for each table.
- Sensitive Type Time Heatmap: Shows the total query number within the selected period for each sensitive type.
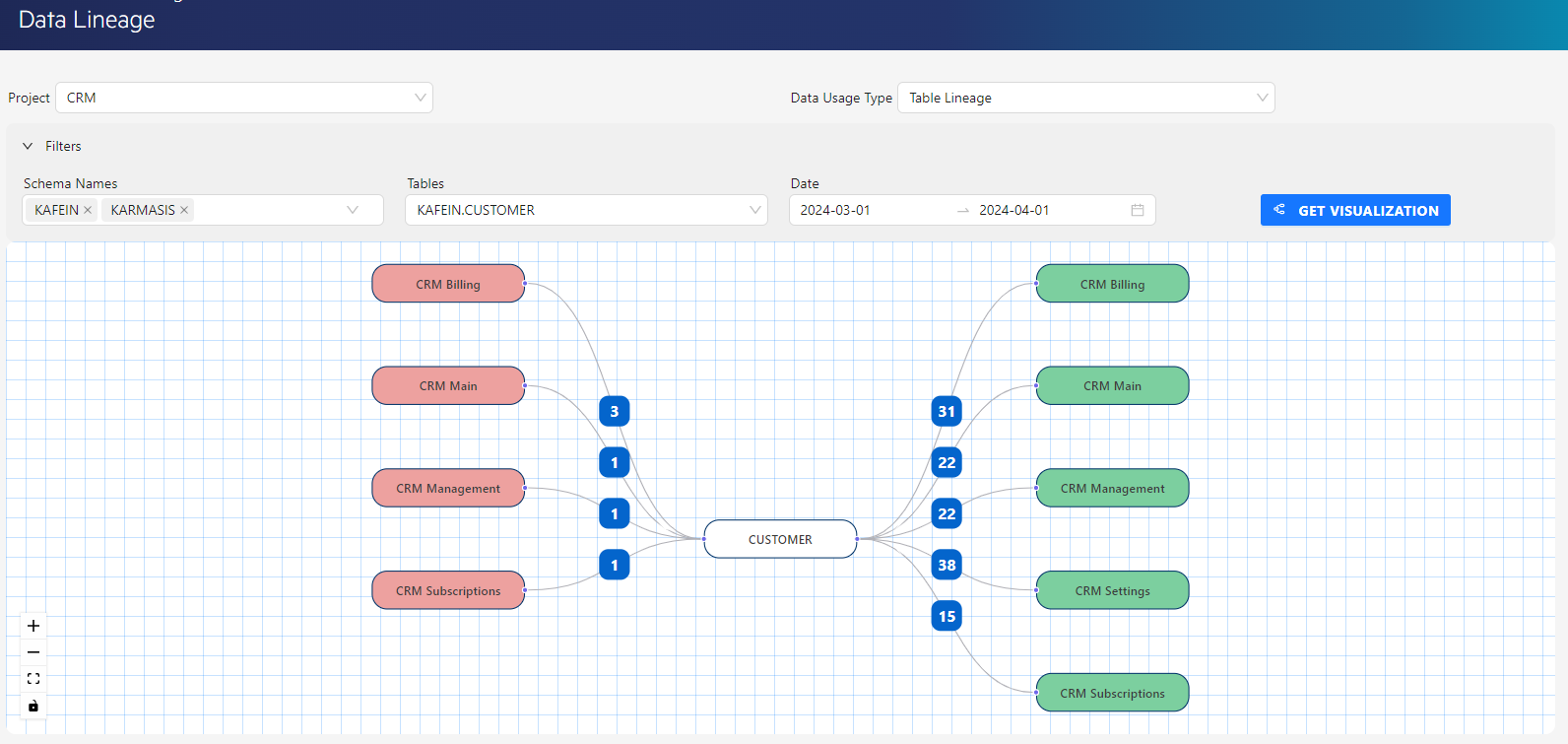
- Data Lineage: Data Lineage creates a map showing all stages, changes, and relationships a table, column, or application goes through, starting from its source. It provides the ability to track the paths where data is created, used, modified, and transferred.The solution provides detailed understanding of data origin, usage, and changes within data management processes.
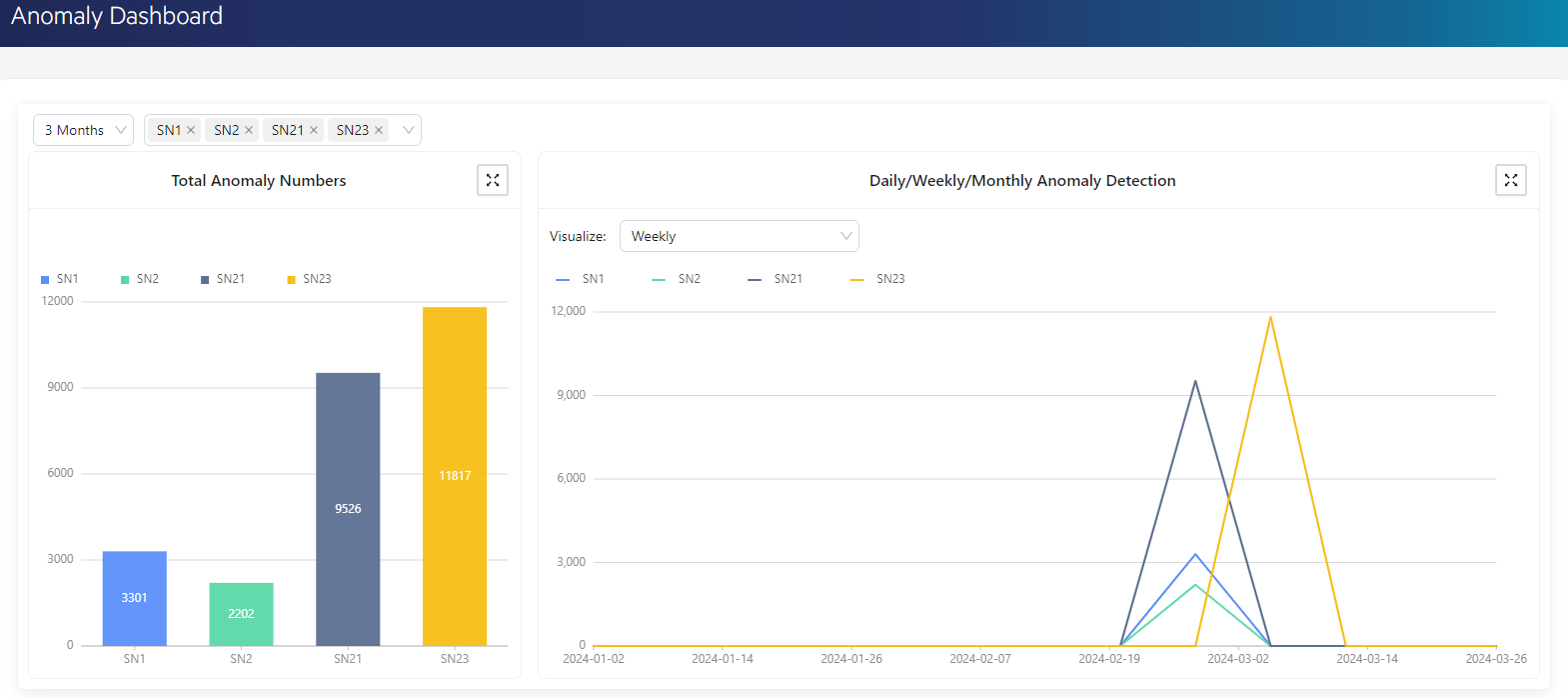
- Anomaly Detection: The Anomaly Engine can detect abnormal conditions from the perspective of users or data sources by analyzing usage data from data sources in real-time. Its purpose is to identify unusual behaviors, outliers, or potential threats that may indicate errors, security breaches, or performance issues.
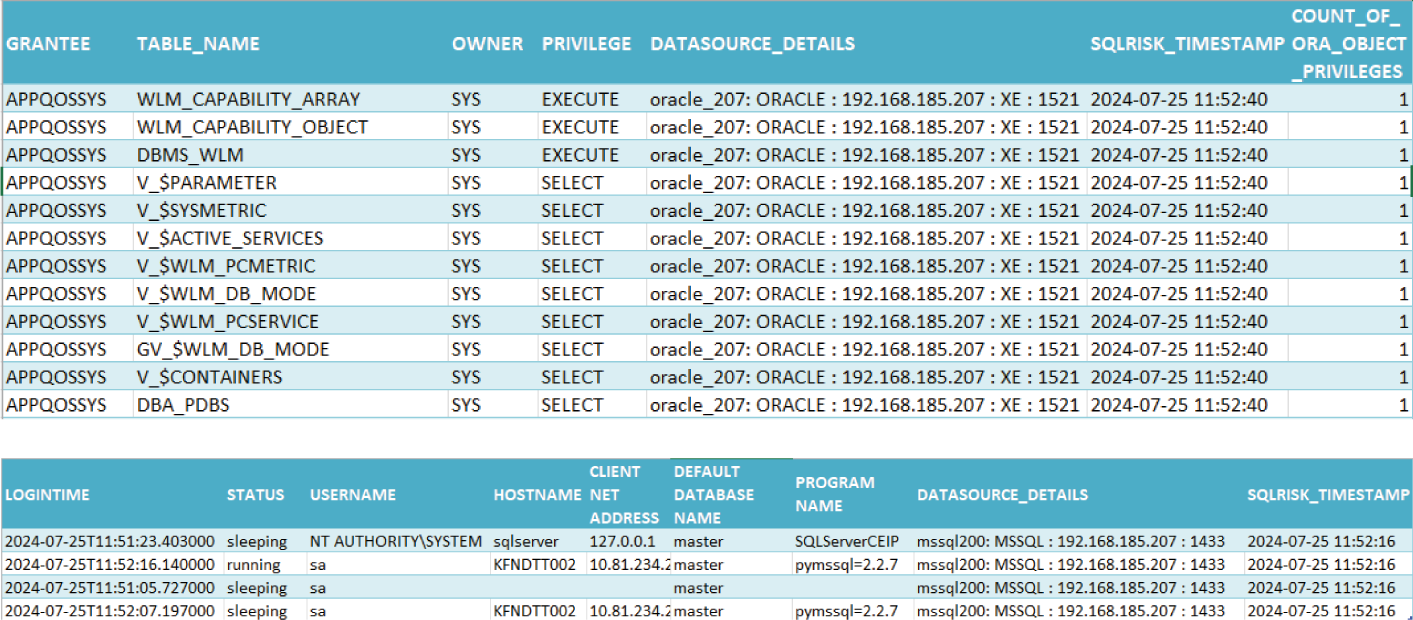
- Data Source Spectrum Reports: Provides extensive user privilege reports for various databases including Oracle, MS SQL, PostgreSQL, MySQL and MongoDB .Reports include user roles, altered privileges, login times, number of administrators and many more.